Blog
Recon-NG
Posted on July 12, 2020 (Last modified on July 15, 2024) • 25 min read • 5,324 wordsComo obter informações de organizações alvo, sua infraestrutura e seus colaboradores sem qualquer interação direta. A Recon-NG quick-start! 😉

Sumário
- Sumário
- O Recon-NG
- Introdução
- Iniciando Recon-NG
- Configuração de proxy
- Organizando workspaces
- Adicionando organizações e seus domínios ao workspace
- Trabalhando com o marketplace e seus módulos
- Executando os módulos e obtendo informações
- Criando Relatório
- Recon-web
- Conclusão
- Apêndice I - Configuração de APIs
O Recon-NG
O Recon-NG, desenvolvido por Tim Tomes, é um framework de reconhecimento construído com o objetivo de prover um ambiente poderoso e customizável para condução de análise passiva a partir de informações públicas em contexto web.
O Recon-NG pode ser baixado em https://github.com/lanmaster53/recon-ng e por padrão já vem instalado no Kali Linux.
Introdução
Como membro do Red Team, você frequentemente enfrenta o dilema de quanto tempo, se houver, de se comprometer com a coleta de informações técnicas.
Nas campanhas é necessário olhar para tudo que está ao redor do alvo a ser analisado, antes mesmo de realizar uma análise ativa diretamente nos recursos conhecidos do alvo, é totalmente viável ter um bom panorama a partir de informações disponíveis publicamente e conhecer melhor o seu alvo de forma passiva. Aí que entramos no conceito de OSINT (Open Source Intelligence).
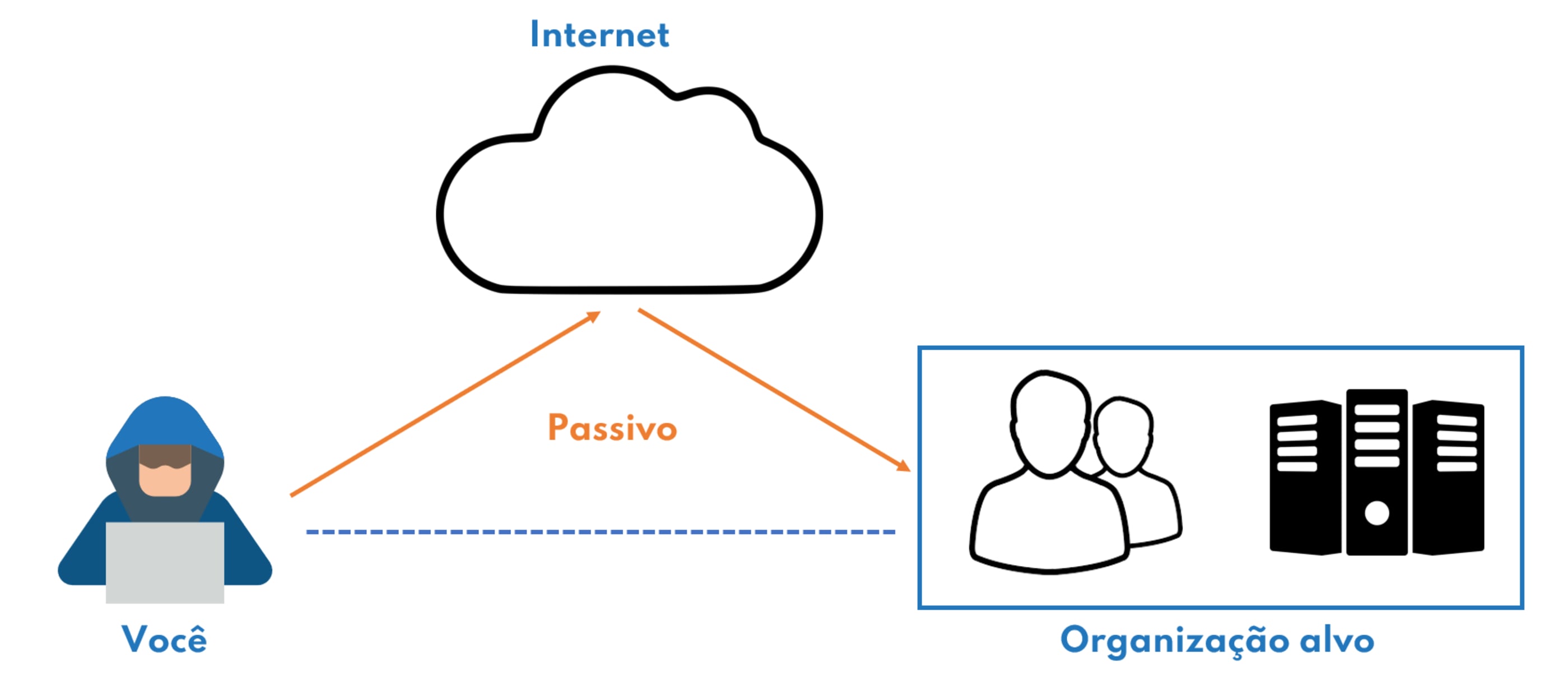

O Recon-NG é apenas uma das ferramentas disponíveis para este tipo de trabalho. Mais opções para cada tipo de atividade pode ser consultada no site https://osintframework.com/.
Abaixo um mapa mental inicial das atividades e suas ferramentas exemplificadas em https://osintframework.com/.

Os motivos que me fizeram a escrever material são:
- Trabalhei com a versão 3 ou 4 (não me lembro) do Recon-NG, e quando me deparei com a versão 5, todos os comandos que eu me lembrava não funcionavam mais…😒
- Quase todo material disponível nos livros que possuo e nos materiais online disponíveis são para versões abaixo da versão 5. Mudou muito a forma de trabalhar com a ferramenta.
- Praticamente não há materiais em Português para a nova versão.
Principais características do Recon-NG
- Mais de 100 módulos disponíveis no marketplace;
- Pela ferramenta ser construída em Python, é relativamente simples de construir seu próprio módulo. https://github.com/lanmaster53/recon-ng/wiki/Development-Guide;
- Através de scripts é possível a coleta de informações praticamente sem interrupção, mesmo que levo algumas horas para terminar. Mais informações em https://github.com/lanmaster53/recon-ng/wiki/Features#automation;
- Web API. https://github.com/lanmaster53/recon-ng/wiki/Development-Guide#web-api;
- Mais informações em https://github.com/lanmaster53/recon-ng/wiki/Features.
Recon-NG - CyberKillChain, Mitre ATT&CK, Bug Bounties
Olhando para as metodologias utilizadas, no modelo CyberKillChain o Recon-NG se situa na fase de Reconhecimento (Recon), como já foi mencionado anteriormente.

Olhando no detalhe para as táticas de PRE-ATT&CK do MITRE, o Recon-NG imediatamente atende aos itens TA0015 (Technical Information Gathering) e TA0016 (People Information Gathering).
| Tactic | Technique ID | Name | Description |
|---|---|---|---|
| Technical Information Gathering | T1250 | Determine domain and IP address space | Domain Names are the human readable names used to represent one or more IP addresses. IP addresses are the unique identifier of computing devices on a network. Both pieces of information are valuable to an adversary who is looking to understand the structure of a network. |
| Technical Information Gathering | T1261 | Enumerate externally facing software applications technologies, languages, and dependencies | Software applications will be built using different technologies, languages, and dependencies. This information may reveal vulnerabilities or opportunities to an adversary. |
| People Information Gathering | T1271 | Identify personnel with an authority/privilege | Personnel internally to a company may have non-electronic specialized access, authorities, or privilege that make them an attractive target for an adversary. One example of this is an individual with financial authority to authorize large transactions. An adversary who compromises this individual might be able to subvert large dollar transfers. |
Em programas de bug bounty como HackerOne ou BugCrowd, em escopos mais abertos você pode utilizar esta ferramenta e automatizá-la para monitorar as empresas quer você busca por vulnerabilidades e consequentemente recompensas. 🤑
Iniciando Recon-NG
root@kali:~# recon-ng
Listando opções
[recon-ng][default] > help
Commands (type [help|?] <topic>):
---------------------------------
back Exits the current context
dashboard Displays a summary of activity
db Interfaces with the workspace's database
exit Exits the framework
help Displays this menu
index Creates a module index (dev only)
keys Manages third party resource credentials
marketplace Interfaces with the module marketplace
modules Interfaces with installed modules
options Manages the current context options
pdb Starts a Python Debugger session (dev only)
script Records and executes command scripts
shell Executes shell commands
show Shows various framework items
snapshots Manages workspace snapshots
spool Spools output to a file
workspaces Manages workspacesConfiguração de proxy
Se precisar configurar um proxy, você pode utilizar a opção options.
recon-ng][Boeing] > options list
Name Current Value Required Description
---------- ------------- -------- -----------
NAMESERVER 8.8.8.8 yes default nameserver for the resolver mixin
PROXY no proxy server (address:port)
THREADS 10 yes number of threads (where applicable)
TIMEOUT 10 yes socket timeout (seconds)
USER-AGENT Recon-ng/v5 yes user-agent string
VERBOSITY 1 yes verbosity level (0 = minimal, 1 = verbose, 2 = debug)Para configurar algo necessário, basta utilizar a seguinte expressão, declarando 192.168.0.1 como proxy:
[recon-ng][Boeing] > option set PROXY 192.168.0.1Se precisar desconfigurar algo, ou vc pode subscrever com o próprio set ou usar o unset.
Organizando workspaces
Sempre que quiser ver todas as opções de uma determinada opção basta usar a tecla TAB para listar.
[recon-ng] > marketplace <TAB>
info install refresh remove searchPrecisamos nos organizar, criaremos um workspace para nosso site.
[recon-ng][default] > workspaces create tiagotavares.io
[recon-ng][tiagotavares.io] > Adicionando organizações e seus domínios ao workspace
Agora vamos começar a inserir informações das empresas que vamos analisar, para teste vamos exemplificar com a Boeing ✈️.
[recon-ng][tiagotavares.io] > db insert companies
company (TEXT): Boeing
description (TEXT): Boeing is the world's largest aerospace company and leading manufacturer.
notes (TEXT):
[*] 1 rows affected.
[recon-ng][tiagotavares.io] >Podemos listar workspaces e companies, como no exemplo abaixo.
[recon-ng][tiagotavares.io] > show companies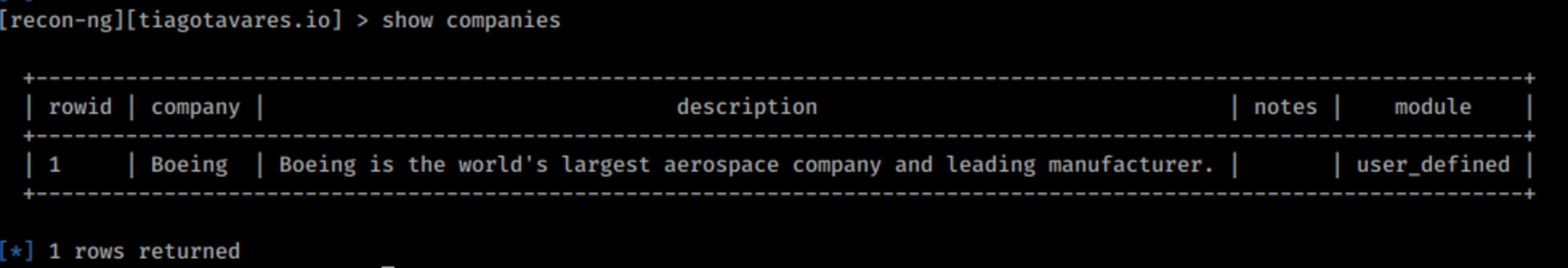
No mesmo workplaces podemos adicionar quantos empresas quisermos. Vamos adicionar agora a concorrente Airbus e o orgulho nacional, a Embraer.

[recon-ng][tiagotavares.io] > db insert companies
company (TEXT): Airbus
description (TEXT):
notes (TEXT):
[*] 1 rows affected.
[recon-ng][tiagotavares.io] > db insert companies
company (TEXT): Embraer
description (TEXT):
notes (TEXT):
[*] 1 rows affected.[recon-ng][tiagotavares.io] > show companies
Vamos adicionar agora seus respectivos domínios para iniciar os trabalhos.
Adicionando boeing.com
[recon-ng][tiago.tavares.io] > db insert domains
domain (TEXT): boeing.com
notes (TEXT):
[*] 1 rows affected.Adicionando airbus.com
[recon-ng][tiago.tavares.io] > db insert domains
domain (TEXT): airbus.com
notes (TEXT):
[*] 1 rows affected.Adicionando embraer.com
[recon-ng][tiago.tavares.io] > db insert domains
domain (TEXT): embraer.com
notes (TEXT):
[*] 1 rows affected.Trabalhando com o marketplace e seus módulos
Precisamos tornar o Recon-ng em algo útil, vamos começar a utilizar o marketplace para começar a dar funções a ferramenta.
Primeiro vamos atualizar a base.
[recon-ng][tiagotavares.io] > marketplace refreshAgora vamos buscar todos os módulos disponíveis. Lembrando que é possível desenvolver seu próprio modulo que atenda melhoras as suas necessidades. 😉
Nas últimas colunas D e K respectivamente mostram informações se o módulo possui dependências ou se ele precisa de alguma chave de API.
[recon-ng][tiagotavares.io] > marketplace search
+---------------------------------------------------------------------------------------------------+
| Path | Version | Status | Updated | D | K |
+---------------------------------------------------------------------------------------------------+
| discovery/info_disclosure/cache_snoop | 1.0 | not installed | 2019-06-24 | | |
| discovery/info_disclosure/interesting_files | 1.1 | not installed | 2020-01-13 | | |
| exploitation/injection/command_injector | 1.0 | not installed | 2019-06-24 | | |
| exploitation/injection/xpath_bruter | 1.2 | not installed | 2019-10-08 | | |
| import/csv_file | 1.1 | not installed | 2019-08-09 | | |
| import/list | 1.1 | not installed | 2019-06-24 | | |
| import/masscan | 1.0 | not installed | 2020-04-07 | | |
| import/nmap | 1.0 | not installed | 2019-06-24 | | |
| recon/companies-contacts/bing_linkedin_cache | 1.0 | not installed | 2019-06-24 | | * |
| recon/companies-contacts/censys_email_address | 1.0 | not installed | 2019-08-22 | | * |
| recon/companies-contacts/pen | 1.1 | not installed | 2019-10-15 | | |
| recon/companies-domains/censys_subdomains | 1.0 | not installed | 2019-08-22 | | * |
| recon/companies-domains/pen | 1.1 | not installed | 2019-10-15 | | |
| recon/companies-domains/viewdns_reverse_whois | 1.0 | not installed | 2019-08-08 | | |
| recon/companies-domains/whoxy_dns | 1.0 | not installed | 2020-06-17 | | * |
| recon/companies-hosts/censys_org | 1.0 | not installed | 2019-08-22 | | * |
| recon/companies-hosts/censys_tls_subjects | 1.0 | not installed | 2019-08-22 | | * |
| recon/companies-multi/github_miner | 1.1 | not installed | 2020-05-15 | | * |
| recon/companies-multi/shodan_org | 1.1 | not installed | 2020-07-01 | * | * |
| recon/companies-multi/whois_miner | 1.1 | not installed | 2019-10-15 | | |
| recon/contacts-contacts/abc | 1.0 | not installed | 2019-10-11 | * | |
| recon/contacts-contacts/mailtester | 1.0 | not installed | 2019-06-24 | | |
| recon/contacts-contacts/mangle | 1.0 | not installed | 2019-06-24 | | |
| recon/contacts-contacts/unmangle | 1.1 | not installed | 2019-10-27 | | |
| recon/contacts-credentials/hibp_breach | 1.2 | not installed | 2019-09-10 | | * |
| recon/contacts-credentials/hibp_paste | 1.1 | not installed | 2019-09-10 | | * |
| recon/contacts-credentials/scylla | 1.2 | not installed | 2020-06-05 | | |
| recon/contacts-domains/migrate_contacts | 1.1 | not installed | 2020-05-17 | | |
| recon/contacts-profiles/fullcontact | 1.1 | not installed | 2019-07-24 | | * |
| recon/credentials-credentials/adobe | 1.0 | not installed | 2019-06-24 | | |
| recon/credentials-credentials/bozocrack | 1.0 | not installed | 2019-06-24 | | |
| recon/credentials-credentials/hashes_org | 1.0 | not installed | 2019-06-24 | | * |
| recon/domains-companies/censys_companies | 1.0 | not installed | 2019-08-22 | | * |
| recon/domains-companies/pen | 1.1 | not installed | 2019-10-15 | | |
| recon/domains-companies/whoxy_whois | 1.1 | not installed | 2020-06-24 | | * |
| recon/domains-contacts/hunter_io | 1.2 | not installed | 2020-04-14 | | * |
| recon/domains-contacts/metacrawler | 1.1 | not installed | 2019-06-24 | * | |
| recon/domains-contacts/pen | 1.1 | not installed | 2019-10-15 | | |
| recon/domains-contacts/pgp_search | 1.4 | not installed | 2019-10-16 | | |
| recon/domains-contacts/whois_pocs | 1.0 | not installed | 2019-06-24 | | |
| recon/domains-contacts/wikileaker | 1.0 | not installed | 2020-04-08 | | |
| recon/domains-credentials/pwnedlist/account_creds | 1.0 | not installed | 2019-06-24 | * | * |
| recon/domains-credentials/pwnedlist/api_usage | 1.0 | not installed | 2019-06-24 | | * |
| recon/domains-credentials/pwnedlist/domain_creds | 1.0 | not installed | 2019-06-24 | * | * |
| recon/domains-credentials/pwnedlist/domain_ispwned | 1.0 | not installed | 2019-06-24 | | * |
| recon/domains-credentials/pwnedlist/leak_lookup | 1.0 | not installed | 2019-06-24 | | |
| recon/domains-credentials/pwnedlist/leaks_dump | 1.0 | not installed | 2019-06-24 | | * |
| recon/domains-credentials/scylla | 1.2 | not installed | 2020-04-14 | | |
| recon/domains-domains/brute_suffix | 1.1 | not installed | 2020-05-17 | | |
| recon/domains-hosts/binaryedge | 1.2 | not installed | 2020-06-18 | | * |
| recon/domains-hosts/bing_domain_api | 1.0 | not installed | 2019-06-24 | | * |
| recon/domains-hosts/bing_domain_web | 1.1 | not installed | 2019-07-04 | | |
| recon/domains-hosts/brute_hosts | 1.0 | not installed | 2019-06-24 | | |
| recon/domains-hosts/builtwith | 1.0 | not installed | 2019-06-24 | | * |
| recon/domains-hosts/censys_domain | 1.0 | not installed | 2019-08-22 | | * |
| recon/domains-hosts/certificate_transparency | 1.2 | not installed | 2019-09-16 | | |
| recon/domains-hosts/findsubdomains | 1.0 | not installed | 2019-06-24 | | |
| recon/domains-hosts/google_site_web | 1.0 | not installed | 2019-06-24 | | |
| recon/domains-hosts/hackertarget | 1.1 | installed | 2020-05-17 | | |
| recon/domains-hosts/mx_spf_ip | 1.0 | not installed | 2019-06-24 | | |
| recon/domains-hosts/netcraft | 1.1 | not installed | 2020-02-05 | | |
| recon/domains-hosts/shodan_hostname | 1.1 | not installed | 2020-07-01 | * | * |
| recon/domains-hosts/ssl_san | 1.0 | not installed | 2019-06-24 | | |
| recon/domains-hosts/threatcrowd | 1.0 | not installed | 2019-06-24 | | |
| recon/domains-hosts/threatminer | 1.0 | not installed | 2019-06-24 | | |
| recon/domains-vulnerabilities/ghdb | 1.1 | not installed | 2019-06-26 | | |
| recon/domains-vulnerabilities/xssed | 1.0 | not installed | 2019-06-24 | | |
| recon/hosts-domains/migrate_hosts | 1.1 | not installed | 2020-05-17 | | |
| recon/hosts-hosts/bing_ip | 1.0 | not installed | 2019-06-24 | | * |
| recon/hosts-hosts/censys_hostname | 1.0 | not installed | 2019-08-22 | | * |
| recon/hosts-hosts/censys_ip | 1.0 | not installed | 2019-08-22 | | * |
| recon/hosts-hosts/censys_query | 1.0 | not installed | 2019-08-22 | | * |
| recon/hosts-hosts/ipinfodb | 1.1 | not installed | 2020-06-08 | | * |
| recon/hosts-hosts/ipstack | 1.0 | not installed | 2019-06-24 | | * |
| recon/hosts-hosts/resolve | 1.0 | not installed | 2019-06-24 | | |
| recon/hosts-hosts/reverse_resolve | 1.0 | not installed | 2019-06-24 | | |
| recon/hosts-hosts/ssltools | 1.0 | not installed | 2019-06-24 | | |
| recon/hosts-hosts/virustotal | 1.0 | not installed | 2019-06-24 | | * |
| recon/hosts-locations/migrate_hosts | 1.0 | not installed | 2019-06-24 | | |
| recon/hosts-ports/binaryedge | 1.0 | not installed | 2019-06-24 | | * |
| recon/hosts-ports/shodan_ip | 1.2 | not installed | 2020-07-01 | * | * |
| recon/locations-locations/geocode | 1.0 | not installed | 2019-06-24 | | * |
| recon/locations-locations/reverse_geocode | 1.0 | not installed | 2019-06-24 | | * |
| recon/locations-pushpins/flickr | 1.0 | not installed | 2019-06-24 | | * |
| recon/locations-pushpins/shodan | 1.1 | not installed | 2020-07-01 | | * |
| recon/locations-pushpins/twitter | 1.1 | not installed | 2019-10-17 | | * |
| recon/locations-pushpins/youtube | 1.1 | not installed | 2019-10-15 | | * |
| recon/netblocks-companies/censys_netblock_company | 1.0 | not installed | 2019-08-22 | | * |
| recon/netblocks-companies/whois_orgs | 1.0 | not installed | 2019-06-24 | | |
| recon/netblocks-hosts/censys_netblock | 1.0 | not installed | 2019-08-22 | | * |
| recon/netblocks-hosts/reverse_resolve | 1.0 | not installed | 2019-06-24 | | |
| recon/netblocks-hosts/shodan_net | 1.1 | installed | 2020-07-01 | * | * |
| recon/netblocks-hosts/virustotal | 1.0 | not installed | 2019-06-24 | | * |
| recon/netblocks-ports/census_2012 | 1.0 | not installed | 2019-06-24 | | |
| recon/netblocks-ports/censysio | 1.0 | not installed | 2019-06-24 | | * |
| recon/ports-hosts/migrate_ports | 1.0 | not installed | 2019-06-24 | | |
| recon/ports-hosts/ssl_scan | 1.0 | not installed | 2020-04-13 | | |
| recon/profiles-contacts/bing_linkedin_contacts | 1.1 | not installed | 2019-10-08 | | * |
| recon/profiles-contacts/dev_diver | 1.1 | not installed | 2020-05-15 | | |
| recon/profiles-contacts/github_users | 1.0 | not installed | 2019-06-24 | | * |
| recon/profiles-profiles/namechk | 1.0 | not installed | 2019-06-24 | | * |
| recon/profiles-profiles/profiler | 1.0 | not installed | 2019-06-24 | | |
| recon/profiles-profiles/twitter_mentioned | 1.0 | not installed | 2019-06-24 | | * |
| recon/profiles-profiles/twitter_mentions | 1.0 | not installed | 2019-06-24 | | * |
| recon/profiles-repositories/github_repos | 1.1 | not installed | 2020-05-15 | | * |
| recon/repositories-profiles/github_commits | 1.0 | not installed | 2019-06-24 | | * |
| recon/repositories-vulnerabilities/gists_search | 1.0 | not installed | 2019-06-24 | | |
| recon/repositories-vulnerabilities/github_dorks | 1.0 | not installed | 2019-06-24 | | * |
| reporting/csv | 1.0 | not installed | 2019-06-24 | | |
| reporting/html | 1.0 | not installed | 2019-06-24 | | |
| reporting/json | 1.0 | not installed | 2019-06-24 | | |
| reporting/list | 1.0 | not installed | 2019-06-24 | | |
| reporting/proxifier | 1.0 | not installed | 2019-06-24 | | |
| reporting/pushpin | 1.0 | not installed | 2019-06-24 | | * |
| reporting/xlsx | 1.0 | not installed | 2019-06-24 | | |
| reporting/xml | 1.1 | not installed | 2019-06-24 | | |
+---------------------------------------------------------------------------------------------------+
D = Has dependencies. See info for details.
K = Requires keys. See info for details.Em nosso exemplo, iremos utilizar os seguintes módulos para realizar nosso trabalho.
| Path | Version | Status | Updated | D | K | Como Configurar |
| ------------------------------------------- | ------- | ------------- | ---------- | --- | --- | --------------- |
| recon/companies-multi/whois_miner | 1.1 | not installed | 2019-10-15 | | | |
| recon/domains-hosts/google_site_web | 1.0 | not installed | 2019-06-24 | | | |
| recon/domains-hosts/brute_hosts | 1.0 | not installed | 2019-06-24 | | | |
| recon/domains-hosts/netcraft | 1.1 | not installed | 2020-02-05 | | | |
| recon/hosts-hosts/resolve | 1.0 | not installed | 2019-06-24 | | | |
| recon/hosts-hosts/reverse_resolve | 1.0 | not installed | 2019-06-24 | | | |
| discovery/info_disclosure/interesting_files | 1.1 | not installed | 2020-01-13 | | | |
| recon/hosts-hosts/ipinfodb | 1.1 | not installed | 2020-06-08 | | * | Aqui! |
| recon/domains-contacts/whois_pocs | 1.0 | not installed | 2019-06-24 | | | |
| recon/contacts-credentials/hibp_paste | 1.2 | not installed | 2019-09-10 | | * | Aqui! |
| recon/companies-multi/github_miner | 1.1 | not installed | 2020-05-15 | | * | Aqui! |
| recon/hosts-ports/shodan_ip | 1.2 | not installed | 2020-07-01 | * | * | Aqui! |
| recon/domains-hosts/shodan_hostname | 1.1 | not installed | 2020-07-01 | * | * | Aqui! |
| recon/netblocks-hosts/shodan_net | 1.1 | installed | 2020-07-01 | * | * | Aqui! |
| reporting/html | 1.0 | not installed | 2019-06-24 | | | |Atenção para a configuração das keys das APIs necessárias. Utilize os link acima para a configuração ou role a página para o fim do post para o passo a passo. A ordem entre configurar e instalar não importa,
Instalando módulos
Vamos instalar todos os módulos que separamos para o nosso teste. Até a versão atual que estou testando, a v5.1.1, só é possível instalar um módulo de cada vez. 😑
[recon-ng] > marketplace install whois-miner
[recon-ng] > marketplace install google_site_web
[recon-ng] > marketplace install brute_hosts
[recon-ng] > marketplace install netcraft
[recon-ng] > marketplace install resolve
[recon-ng] > marketplace install reverse_resolve
[recon-ng] > marketplace install interesting_files
[recon-ng] > marketplace install ipinfodb
[recon-ng] > marketplace install whois_pocs
[recon-ng] > marketplace install hibp_paste
[recon-ng] > marketplace install scylla
[recon-ng] > marketplace install github_miner
[recon-ng] > marketplace install shodan_ip
[recon-ng] > marketplace install shodan_hostname
[recon-ng] > marketplace install shodan_net
[recon-ng] > marketplace install htmlExecutando os módulos e obtendo informações
Com os nossos módulos instalados, vamos configurá-los e executá-los.
whois_miner
Neste, vamos deixar a opção default e executar.
[recon-ng][tiagotavares.io] > modules load whois_miner
[recon-ng][tiagotavares.io][whois_miner] > info
Name: Whois Data Miner
Author: Tim Tomes (@lanmaster53)
Version: 1.1
Description:
Uses the ARIN Whois RWS to harvest companies, locations, netblocks, and contacts associated with the
given company search string. Updates the respective tables with the results.
Options:
Name Current Value Required Description
------ ------------- -------- -----------
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT company FROM companies WHERE company IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
Comments:
* Wildcard searches are allowed using the "*" character.
* Validate results of the SEARCH string with these URLs:
- http://whois.arin.net/rest/orgs;name=<SEARCH>
- http://whois.arin.net/rest/customers;name=<SEARCH>[recon-ng][tiagotavares.io][whois_miner] > options set SOURCE boeing[recon-ng][tiagotavares.io][whois_miner] > run
[*] URL: http://whois.arin.net/rest/orgs;name=boeing
[*] No ORGS found.
[*] URL: http://whois.arin.net/rest/customers;name=boeing
[*] No CUSTOMERS found.whois_pocs
[recon-ng][tiagotavares.io] > modules load whois_pocs
[recon-ng][tiagotavares.io][whois_pocs] > info
Name: Whois POC Harvester
Author: Tim Tomes (@lanmaster53)
Version: 1.0
Description:
Uses the ARIN Whois RWS to harvest POC data from whois queries for the given domain. Updates the
'contacts' table with the results.
Options:
Name Current Value Required Description
------ ------------- -------- -----------
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT domain FROM domains WHERE domain IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
[recon-ng][tiagotavares.io][whois_pocs] > [recon-ng][tiagotavares.io][whois_pocs] > options set SOURCE boeing.com[recon-ng][tiagotavares.io][whois_pocs] > run
...
...
...
[*] --------------------------------------------------
[*] URL: http://whois.arin.net/rest/poc/AWO19-ARIN
[*] Country: United States
[*] Email: JohnDoe@boeing.com
[*] First_Name: Al
[*] Last_Name: Wood
[*] Middle_Name: None
[*] Notes: None
[*] Phone: None
[*] Region: Seal Beach, CA
[*] Title: Whois contact
[*] --------------------------------------------------
-------
SUMMARY
-------
[*] 159 total (80 new) contacts found.
[recon-ng][tiagotavares.io][whois_pocs] >google_site_web
[recon-ng][tiagotavares.io] > modules load google_site_webConfigure o domínio inicial que será realizada a busca.
[recon-ng][tiagotavares.io][google_site_web] > options set SOURCE boeing.comRode o módulo. Abaixo foram identificado 27 hosts, mas a busca parou após o Captcha do Google, que precisará ser bypassado.
[recon-ng][tiagotavares.io][google_site_web] > run
----------
BOEING.COM
----------
...
...
...
...
Google CAPTCHA triggered. No bypass available.
-------
SUMMARY
-------
[*] 27 total (27 new) hosts found.brute_hosts
[recon-ng][tiagotavares.io] > modules load brute_hosts
[recon-ng][tiagotavares.io][brute_hosts] > options set SOURCE boeing.com
[recon-ng][tiagotavares.io][brute_hosts] > run
...
...
...
[*] zera.boeing.com => No record found.
[*] zeus.boeing.com => No record found.
[*] zlog.boeing.com => No record found.
[*] zm.boeing.com => No record found.
[*] zulu.boeing.com => No record found.
[*] zw.boeing.com => No record found.
-------
SUMMARY
-------
[*] 55 total (42 new) hosts found.ipinfodb
[recon-ng][tiagotavares.io] > modules load infodb
[recon-ng][tiagotavares.io][ipinfodb] > info
Name: IPInfoDB GeoIP
Author: Tim Tomes (@lanmaster53)
Version: 1.1
Keys: ipinfodb_api
Description:
Leverages the ipinfodb.com API to geolocate a host by IP address. Updates the 'hosts' table with the
results.
Options:
Name Current Value Required Description
------ ------------- -------- -----------
LIMIT True yes toggle rate limiting
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT ip_address FROM hosts WHERE ip_address IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
Comments:
* Free API access requires the use of rate limiting.[recon-ng][tiagotavares.io][ipinfodb] > runshodan_ip
[recon-ng][tiagotavares.io] > modules load shodan_ip
[recon-ng][tiagotavares.io][shodan_ip] > info
Name: Shodan IP Enumerator
Author: Tim Tomes (@lanmaster53) and Matt Puckett (@t3lc0) & Ryan Hays (@_ryanhays)
Version: 1.2
Keys: shodan_api
Description:
Harvests port information from the Shodan API by using the 'ip' search operator. Updates the 'ports'
table with the results.
Options:
Name Current Value Required Description
------ ------------- -------- -----------
LIMIT 1 yes limit number of api requests per input source (0 = unlimited)
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT ip_address FROM hosts WHERE ip_address IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputsNão é necessário realizar nenhum configuração adicional além das configurações de chave de API.
[recon-ng][tiagotavares.io][shodan_ip] > run
...
...
...
-------
SUMMARY
-------
[*] 15 total (13 new) ports found.netcraft
[recon-ng][tiagotavares.io] > modules load netcraft
[recon-ng][tiagotavares.io][netcraft] > info
Name: Netcraft Hostname Enumerator
Author: thrapt (thrapt@gmail.com)
Version: 1.1
Description:
Harvests hosts from Netcraft.com. Updates the 'hosts' table with the results.
Options:
Name Current Value Required Description
------ ------------- -------- -----------
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT domain FROM domains WHERE domain IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs[recon-ng][tiagotavares.io][netcraft] > options set SOURCE boeing.com[recon-ng][tiagotavares.io][netcraft] > run
...
...
...
-------
SUMMARY
-------
[*] 9 total (2 new) hosts found.resolve
[recon-ng][tiagotavares.io] > modules load recon/hosts-hosts/resolve
[recon-ng][tiagotavares.io][resolve] > info
Name: Hostname Resolver
Author: Tim Tomes (@lanmaster53)
Version: 1.0
Description:
Resolves the IP address for a host. Updates the 'hosts' table with the results.
Options:
Name Current Value Required Description
------ ------------- -------- -----------
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT host FROM hosts WHERE host IS NOT NULL AND ip_address IS NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
Comments:
* Note: Nameserver must be in IP form.
[recon-ng][tiagotavares.io][resolve] > Aqui não configuraremos nada! Pois ele obterá o IP dos domínios já obtidos!
[recon-ng][tiagotavares.io][resolve] > run
...
...
...
[*] active.boeing.com => 130.76.22.22
[*] securelogon.boeing.com => 130.76.144.230
[*] securelogon.boeing.com => 130.76.144.227
-------
SUMMARY
-------
[*] 21 total (21 new) hosts found.
[recon-ng][tiagotavares.io][resolve] > reverse_resolve
[recon-ng][tiagotavares.io] > modules load recon/hosts-hosts/reverse_resolve
[recon-ng][tiagotavares.io][reverse_resolve] > info
Name: Reverse Resolver
Author: John Babio (@3vi1john), @vulp1n3, and Tim Tomes (@lanmaster53)
Version: 1.0
Description:
Conducts a reverse lookup for each IP address to resolve the hostname. Updates the 'hosts' table
with the results.
Options:
Name Current Value Required Description
------ ------------- -------- -----------
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT ip_address FROM hosts WHERE ip_address IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
[recon-ng][tiagotavares.io][reverse_resolve] >[recon-ng][tiagotavares.io][reverse_resolve] > run
...
...
...
-------
SUMMARY
-------
[*] 89 total (11 new) hosts found.hibp_paste
[recon-ng][tiagotavares.io] > modules load hibp_paste
[recon-ng][tiagotavares.io][hibp_paste] > info
Name: Have I been pwned? Paste Search
Author: Tim Tomes (@lanmaster53) and Geoff Pamerleau (@_geoff_p_)
Version: 1.1
Keys: hibp_api
Description:
Leverages the haveibeenpwned.com API to determine if email addresses have been published to various
paste sites. Adds compromised email addresses to the 'credentials' table.
Options:
Name Current Value Required Description
-------- ------------- -------- -----------
DOWNLOAD True yes download pastes
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT email FROM contacts WHERE email IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
Comments:
* Paste sites supported: Pastebin, Pastie, Slexy, Ghostbin, QuickLeak, JustPaste, AdHocUrl, and
OptOut.The HIBP API is rate limited to 1 request per 1.5 seconds.[recon-ng][tiagotavares.io][hibp_paste] > run
[*] --------------------------------------------------
[*] Hash: None
[*] Leak: None
[*] Notes: None
[*] Password: None
[*] Type: None
[*] Username: LeakedEmail@boeing.com
[*] --------------------------------------------------
...
...
...
[*] john.doe@boeing.com => Not Found.
-------
SUMMARY
-------
[*] 4 total (0 new) contacts found.
[*] 4 total (4 new) credentials found.github_miner
[recon-ng][tiagotavares.io] > modules load github_miner
[recon-ng][tiagotavares.io][github_miner] > info
Name: Github Resource Miner
Author: Tim Tomes (@lanmaster53)
Version: 1.1
Keys: github_api
Description:
Uses the Github API to enumerate repositories and member profiles associated with a company search
string. Updates the respective tables with the results.
Options:
Name Current Value Required Description
----------- ------------- -------- -----------
IGNOREFORKS True yes ignore forks
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT company FROM companies WHERE company IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
[recon-ng][tiagotavares.io][github_miner] > run
------
BOEING
------interesting_files
[recon-ng][tiagotavares.io] > modules load interesting_files
[recon-ng][tiagotavares.io][interesting_files] > info
Name: Interesting File Finder
Author: Tim Tomes (@lanmaster53), thrapt (thrapt@gmail.com), Jay Turla (@shipcod3), and Mark Jeffery
Version: 1.1
Description:
Checks hosts for interesting files in predictable locations.
Options:
Name Current Value Required Description
-------- ------------- -------- -----------
DOWNLOAD True yes download discovered files
PORT 80 yes request port
PROTOCOL http yes request protocol
SOURCE default yes source of input (see 'info' for details)
Source Options:
default SELECT DISTINCT host FROM hosts WHERE host IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
Comments:
* Files: robots.txt, sitemap.xml, sitemap.xml.gz, crossdomain.xml, phpinfo.php, test.php, elmah.axd,
server-status, jmx-console/, admin-console/, web-console/
* Google Dorks:
- inurl:robots.txt ext:txt
- inurl:elmah.axd ext:axd intitle:"Error log for"
- inurl:server-status "Apache Status"
[recon-ng][tiagotavares.io][interesting_files] >Vai demorar um bocado esta parte, você pode ir dormir e voltar para obter o resultado. Porque ele vai analisar cada domínio e subdomínio.
[recon-ng][tiagotavares.io][interesting_files] > run
[*] http://m.shop.boeing.com:80/robots.txt => 404
[*] http://m.shop.boeing.com:80/sitemap.xml => 404
[*] http://m.shop.boeing.com:80/sitemap.xml.gz => 404
[*] http://m.shop.boeing.com:80/crossdomain.xml => 404
[*] http://m.shop.boeing.com:80/phpinfo.php => 404
[*] http://m.shop.boeing.com:80/test.php => 404
[*] http://m.shop.boeing.com:80/elmah.axd => 404
[*] http://m.shop.boeing.com:80/server-status => 404
[*] http://m.shop.boeing.com:80/jmx-console/ => Error
[*] http://m.shop.boeing.com:80/admin-console/ => Error
[*] http://m.shop.boeing.com:80/web-console/ => Error
[*] http://mft.boeing.com:80/robots.txt => Error
...Exibindo na tela informações coletadas
Antes de se gerar qualquer relatório, podemos visualizar todas as informações que estão organizadas em categorias. Estas categorias podem ser listadas e exibidas como no exemplo abaixo.
[recon-ng][tiagotavares.io] > show <TAB>
companies hosts ports vulnerabilities
contacts leaks profiles
credentials locations pushpins
domains netblocks repositories Mostrando todos os hosts coletados em nosso trabalho.
[recon-ng][tiagotavares.io] > show hosts
Criando Relatório
html
[recon-ng][tiagotavares.io] > modules load html
[recon-ng][tiagotavares.io][html] > info
Name: HTML Report Generator
Author: Tim Tomes (@lanmaster53)
Version: 1.0
Description:
Creates an HTML report.
Options:
Name Current Value Required Description
-------- ------------- -------- -----------
CREATOR yes use creator name in the report footer
CUSTOMER yes use customer name in the report header
FILENAME /root/.recon-ng/workspaces/tiagotavares.io/results.html yes path and filename for report output
SANITIZE True yes mask sensitive data in the report[recon-ng][tiagotavares.io][html] > options set CREATOR TT
CREATOR => TT
[recon-ng][tiagotavares.io][html] > options set CUSTOMER Boeing
CUSTOMER => Boeing[recon-ng][tiagotavares.io][html] > run
[*] Report generated at '/root/.recon-ng/workspaces/tiagotavares.io/results.html'.Agora basta abrir o nosso relatório em HTML.
root@kali:~# firefox /root/.recon-ng/workspaces/tiagotavares.io/results.html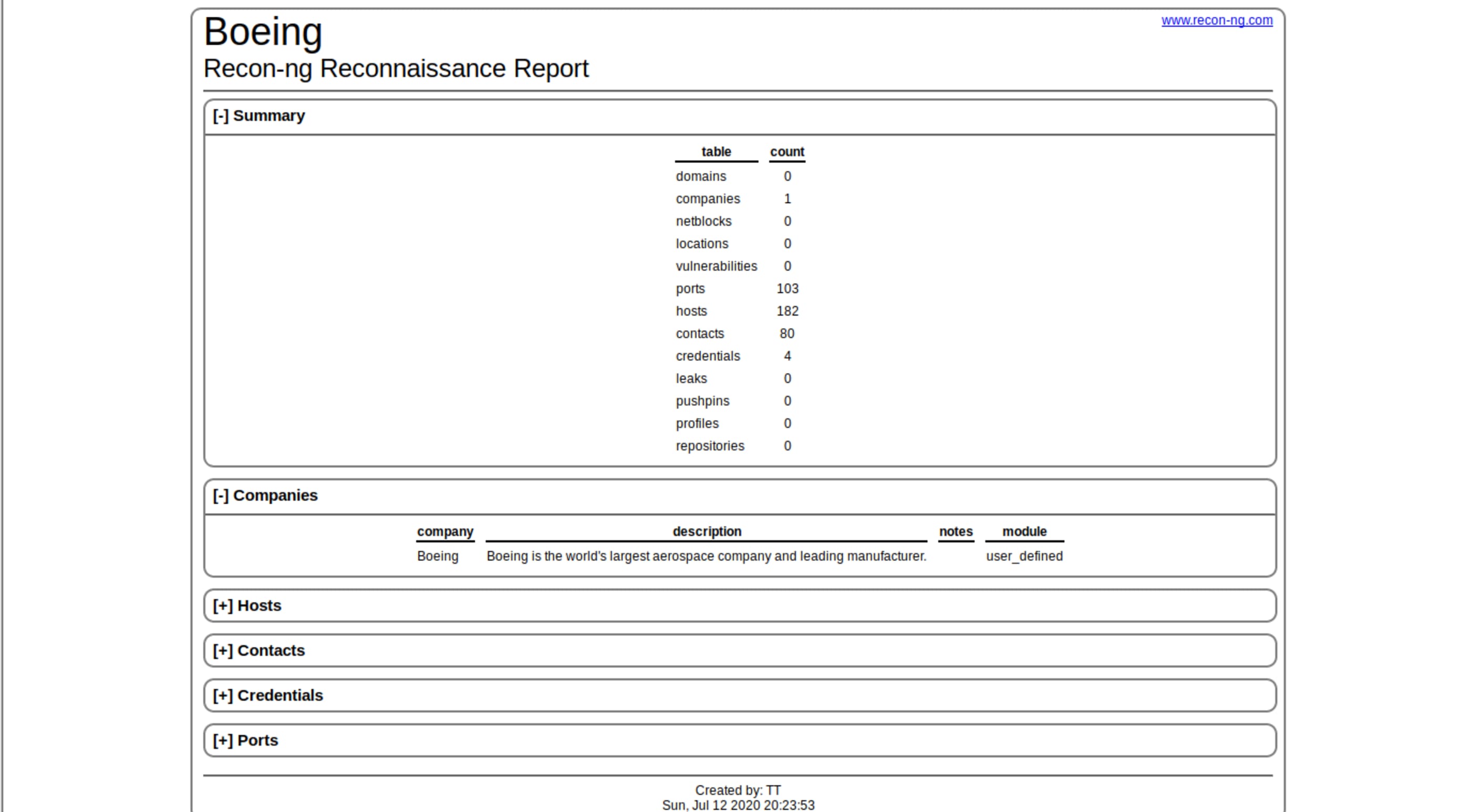
Recon-web
No capítulo anterior foi mostrar a geração de um relatório em HTML e também como exibir resultados na tela do terminal, mas é possível acessar as informações em uma plataforma web com o recon-web.
root@kali:~# recon-web
*************************************************************************
* Welcome to Recon-web, the analytics and reporting engine for Recon-ng!
* This is a web-based user interface. Open the URL below in your browser to begin.
* Recon-web includes the Recon-API, which can be accessed via the `/api/` URL.
*************************************************************************
[*] Marketplace disabled.
[*] Version check disabled.
* Workspace initialized: default
* Running on http://127.0.0.1:5000/ (Press CTRL+C to quit)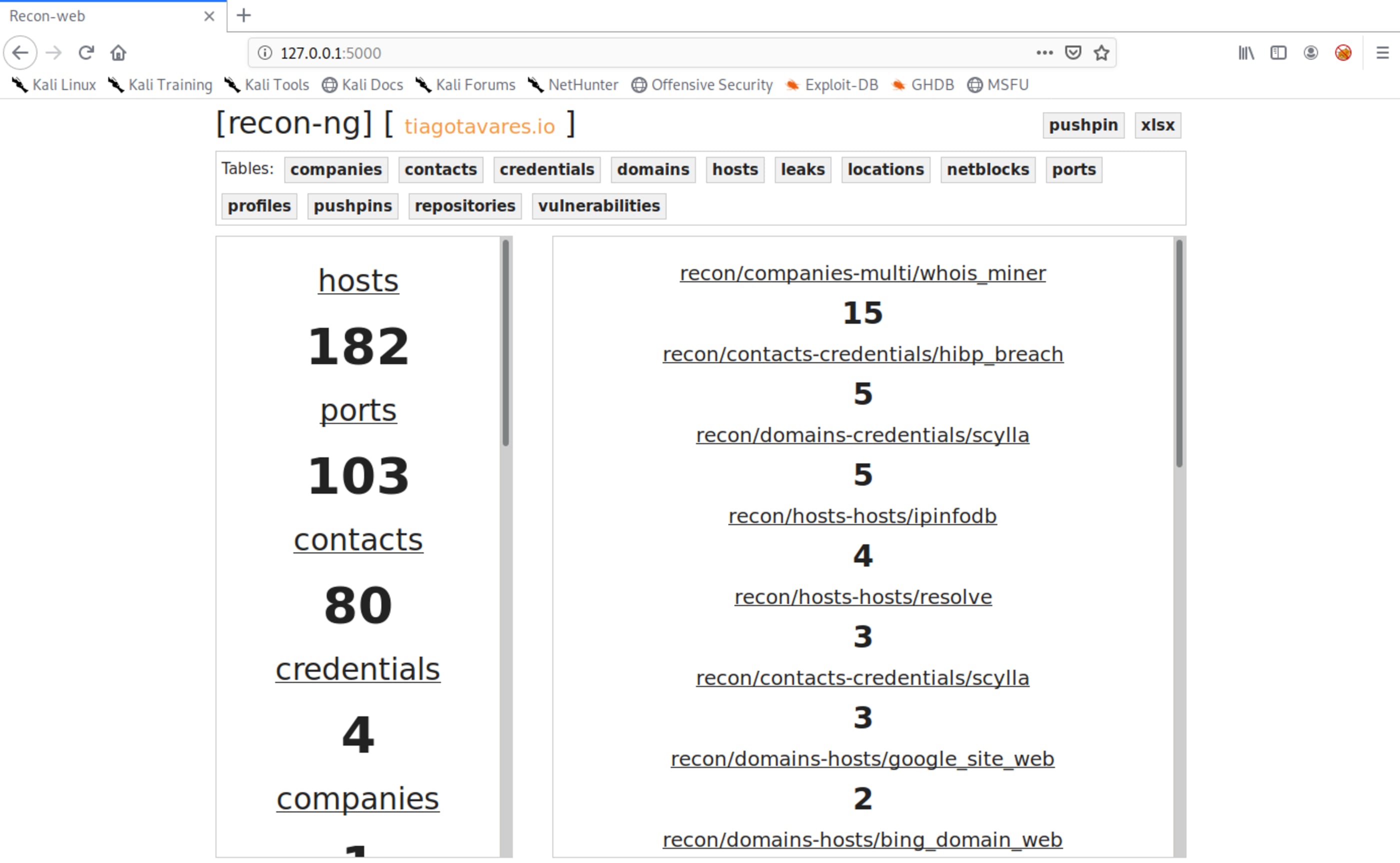
Escolha o workspace onde realizou o trabalho anterior.
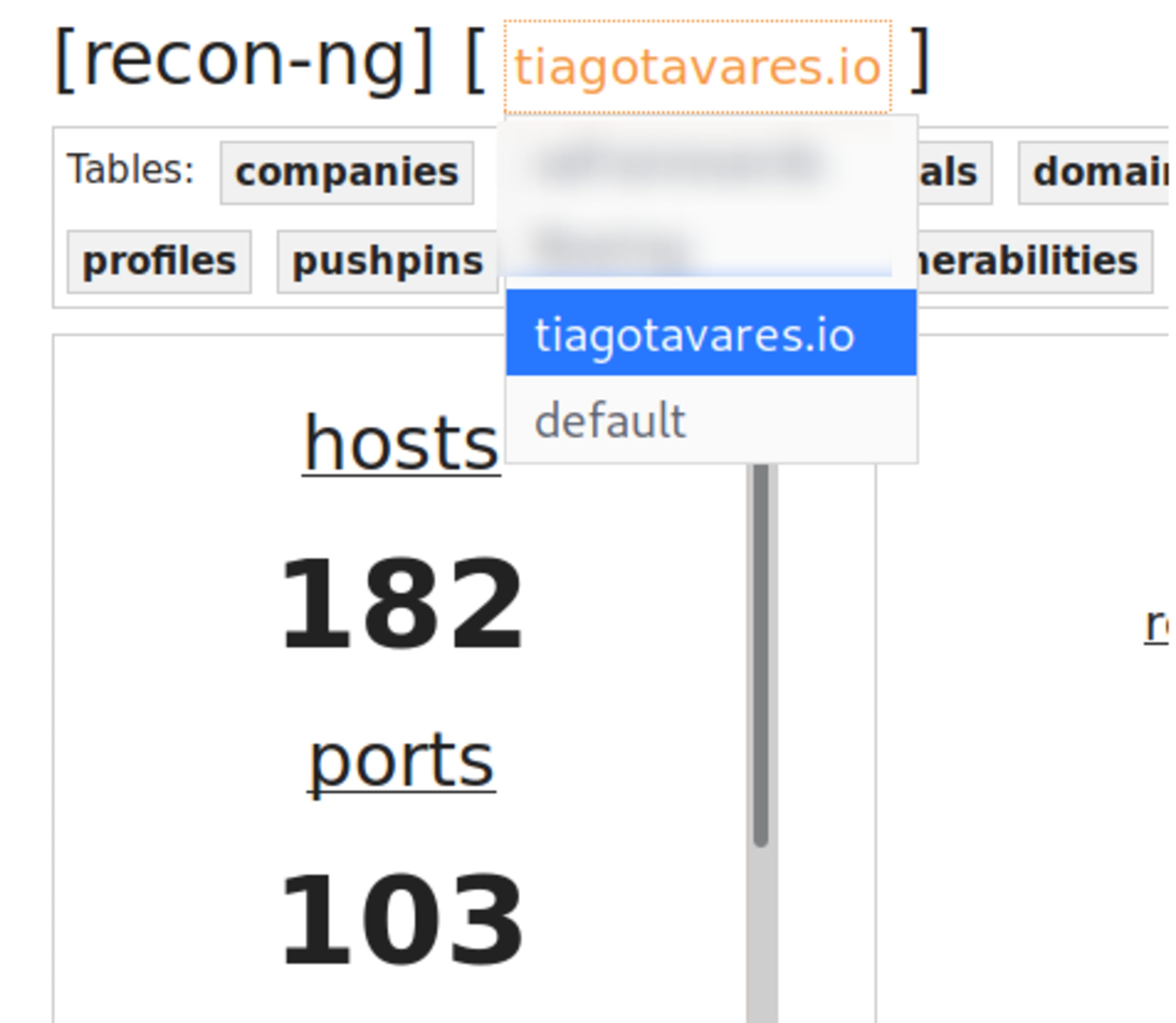
Agora você pode exibir as informações das tabelas de informações criadas pelo Recon-NG, criando filtros e exportando no formato que desejar.

Conclusão
A única coisa que posso concluir sem enrolação é que este framework e seus módulos podem perfeitamente substituir uma infinidade de ferramentas que você utiliza para realizar o reconhecimento de organizações, sem muito trabalho para configuração e maleável para trabalhar em qualquer tipo de ambiente, como por exemplo em containers.
Obrigado pela sua atenção e use o campo de comentários para para comentar e criticar! 😃

Apêndice I - Configuração de APIs
IPinfoDB
Site: https://ipinfodb.com/
Módulos dependentes deste tutorial: ipinfodb
Procedimento:
Crie uma conta ou utilize sua conta do Google para facilitar a criação.

Infelizmente ele só vai permitir resquisições após especificar exatamente de qual iP serão feitas.

Agora é só copiar a chave de API…
… e configurar o recon-ng.
[recon-ng][tiagotavares.io] > keys add ipinfodb_api 94cfe253....a790
[*] Key 'ipinfodb_api' added.Github
Site: https://github.com/
Módulos dependentes deste tutorial: github_api
Procedimento:
Crie um perfil no Github caso não possua.
Vá até a opção Settings.

Depois procure pela opção Developer settings –> Personal access tokens –> Generate new token.
Para fins de teste, vamos apenas dar a permissão de acessar repositórios públicos.
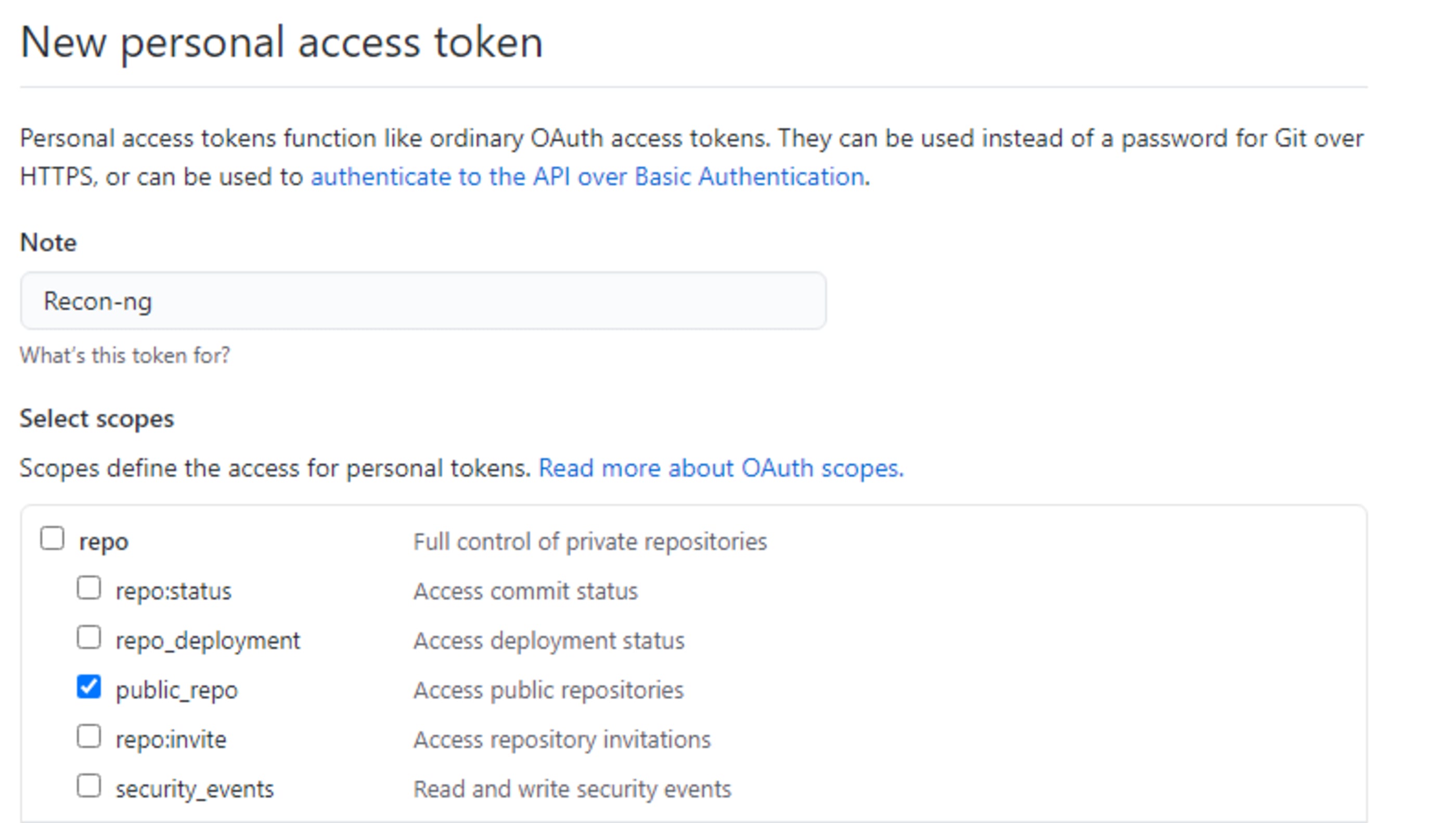
Pronto! Assim como diz mensagem, copie o token e guarde caso precise para outros fins, pois uma vez configurado no recon-ng o token ficará salvo.

Adicionando a chave no recon-ng.
[recon-ng][tiagotavares.io] > keys add github_api 00783....
[*] Key 'github_api' added.HaveIBeenPwned
Site: https://haveibeenpwned.com/
Preço: US$3,50
Módulos dependentes deste tutorial: hibp_api
Procedimento:
Acesse o link de API. Em seguida preencha com seu email.

Logo em seguida você receberá um email para confirmação. Basta clicar em Verify my email.

Para testar, vou comprar um mês de licença.

Pronto, temos a nossa chave!

Agora vamos adicionar a chave ao recon-ng.
[recon-ng][tiagotavares.io] > keys add hibp_api d8e...
[*] Key 'hibp_api' added.Shodan
Site: https://www.shodan.io/
Módulos dependentes deste tutorial: shodan_hostname, shodan_ip, shodan_net
Procedimento:
Acesse a sua conta ou crie uma caso necessário. Depois clique em My Account.

Depois é só copiar a chave de API gerada por ele.
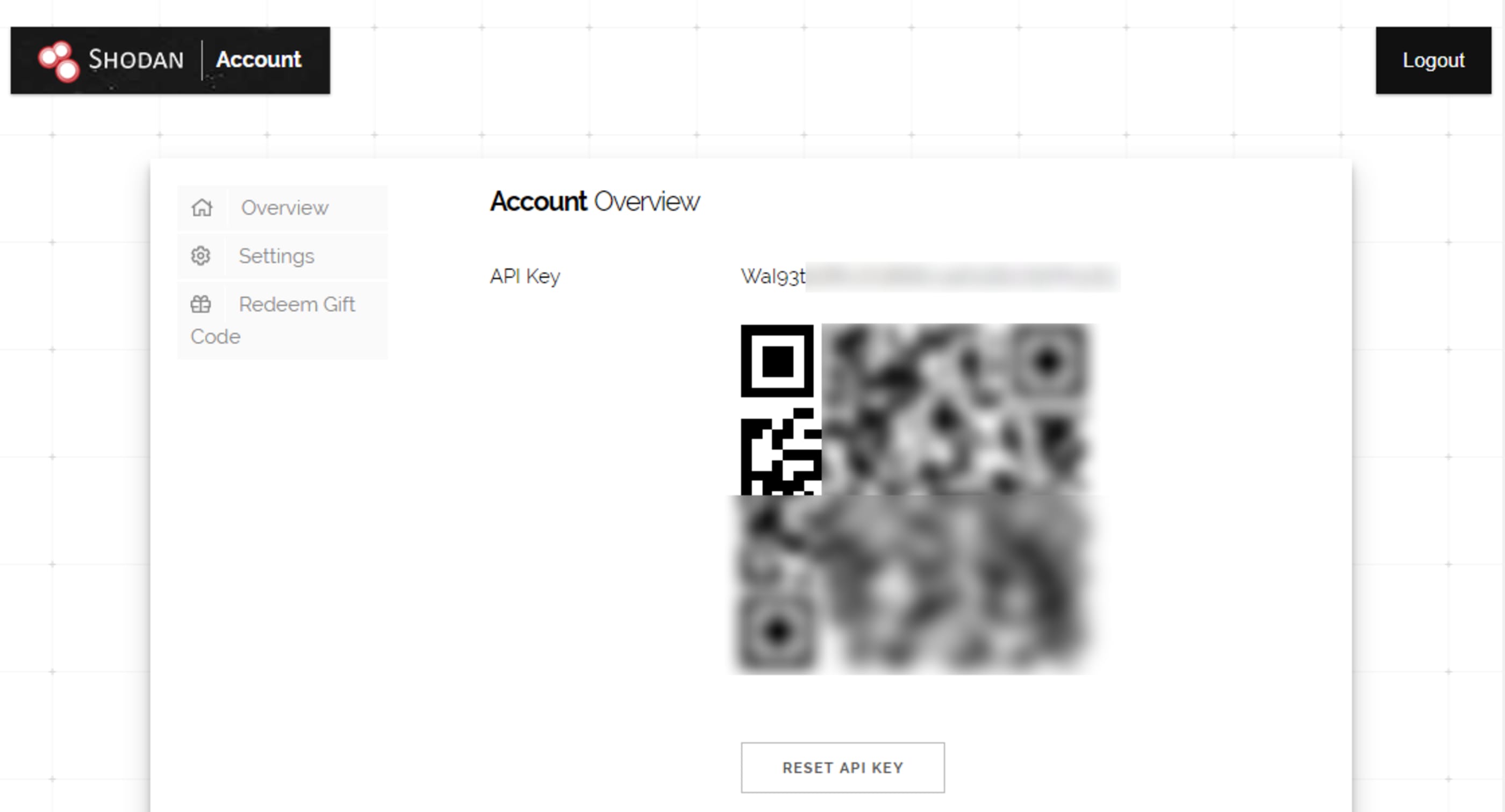
Vamos adicionar a chave ao recon-ng.
[recon-ng][tiagotavares.io] > keys add shodan_api WaI93t.....
[*] Key 'shodan_api' added.